
With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?
One of the best ways to take complete control over your device is to install a custom ROM. A typical custom ROM comes without Google's core apps (Gapps), but you would typically install the separate Gapps package to get them back. However, if you want more freedom and privacy, you would just skip the Gapps package and go with MicroG instead.
You should note that many apps require Google Play Services to work correctly; otherwise, there would be no point in having them installed. MicroG injects a modified version of those core Google services required by most apps, but without all of the tracking that comes with having a Google account. This increases your level of privacy and can even improve battery life as well.
Requirements
Step 1: Make Sure Your ROM Supports Signature Spoofing
Just about all custom ROMs support signature faking by default, which is used to make the system think the real Google Play Services are installed. It is required and necessary for this whole thing to work. You might need to double-check the place you got your custom ROM from to see if it does support signature faking in the first place for MicroG.
Step 2: Skip the Gapps Installation
At this point, you should already have picked out a custom ROM you plan on flashing to your device, and it should have support for signature faking. As mentioned before, you would typically install a Gapps package after flashing a ROM to get the Google services back onto your device. However, to use MicroG, you must make sure you do not install a Gapps package at all when following this guide.
If you did install Gapps by accident (second nature), go ahead and flash the custom ROM again and wipe data to be safe. After you take care of that, boot into the operating system, and make sure the Google apps and services are not present, then you can move onto the next step.
Step 3: Install MicroG for Your Device
In the past, to get the entire MicroG package to work, you would have been required to download multiple separate apps. However, NanoDroid has now come along to simplify things with a single ZIP file that you can flash right in a custom recovery, such as TWRP. There's also a newer and more convenient Magisk module that's perfect for the root users out there. You can't go wrong with either method!
For TWRP Users
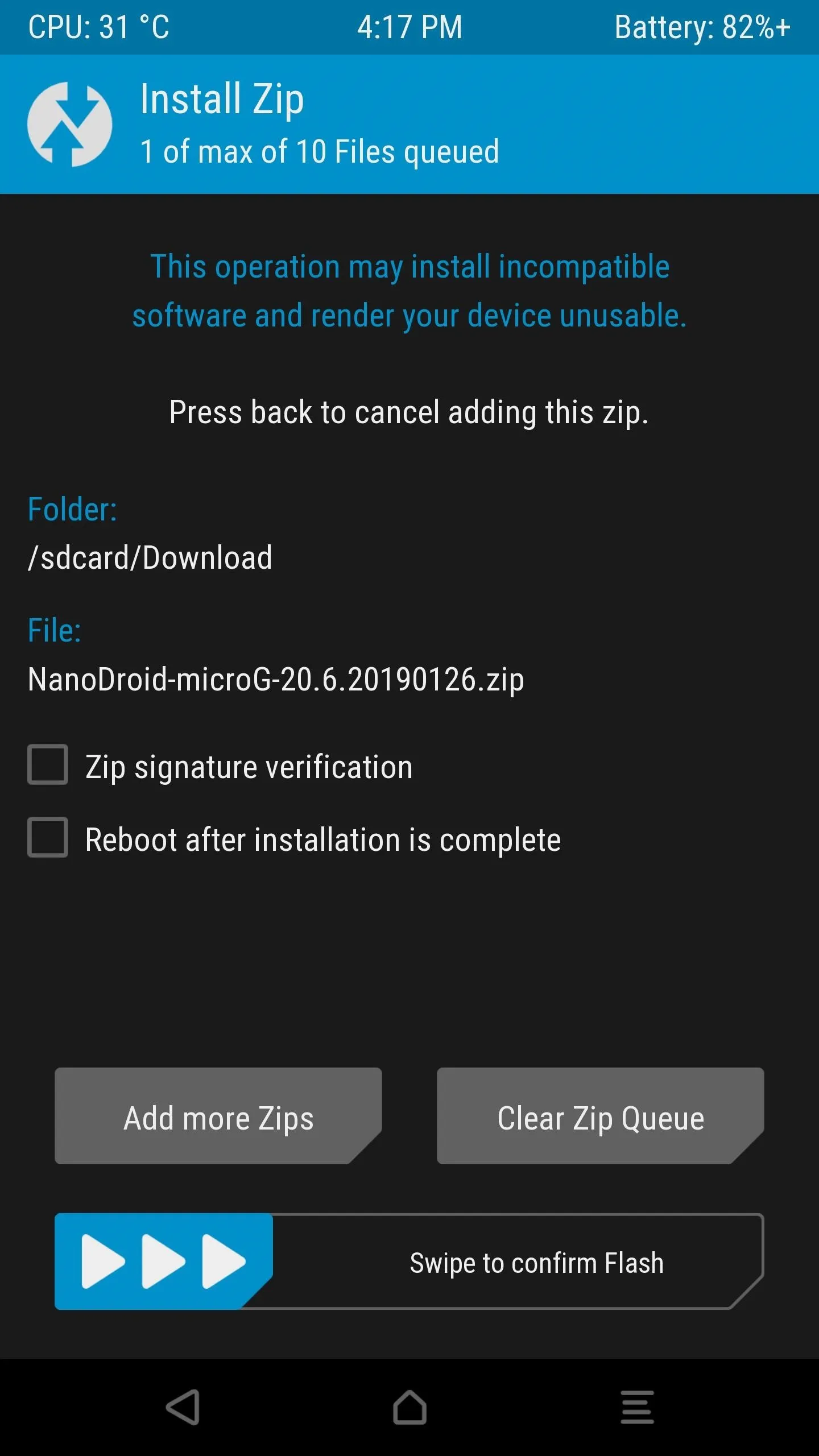
For all of the TWRP people out there who like to keep things as simple as possible, installing NanoDroid with MicroG baked right into it couldn't be any easier. To get started, hit up the download link below and save the file onto your Android phone's internal storage via the "Download" folder.
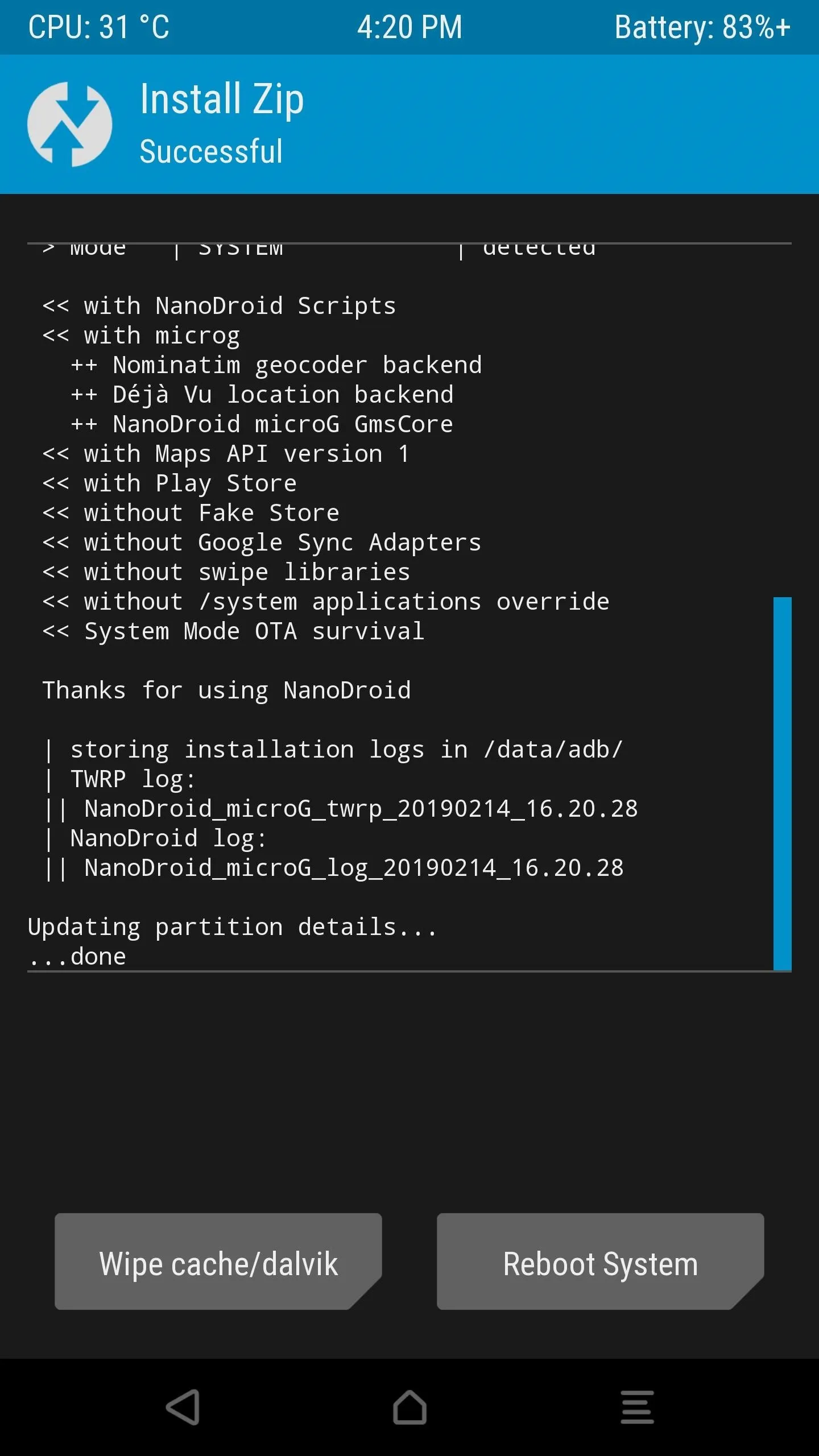
Once you download the file, go ahead and boot into recovery mode to the TWRP main screen. Tap "Install," browse for the location where you stored the NanoDroid file, tap it once, then swipe the slider to begin the installation. After it finishes the install process, you can reboot your device, then you can head onto the next step below.


For Magisk Users
For the root users, developer nift4 (previously Hieu Van) has cooked up a special Magisk module for getting the job done systemlessly without needing to rely on TWRP. To get MicroG up and running through Magisk, follow the quick instructions below.
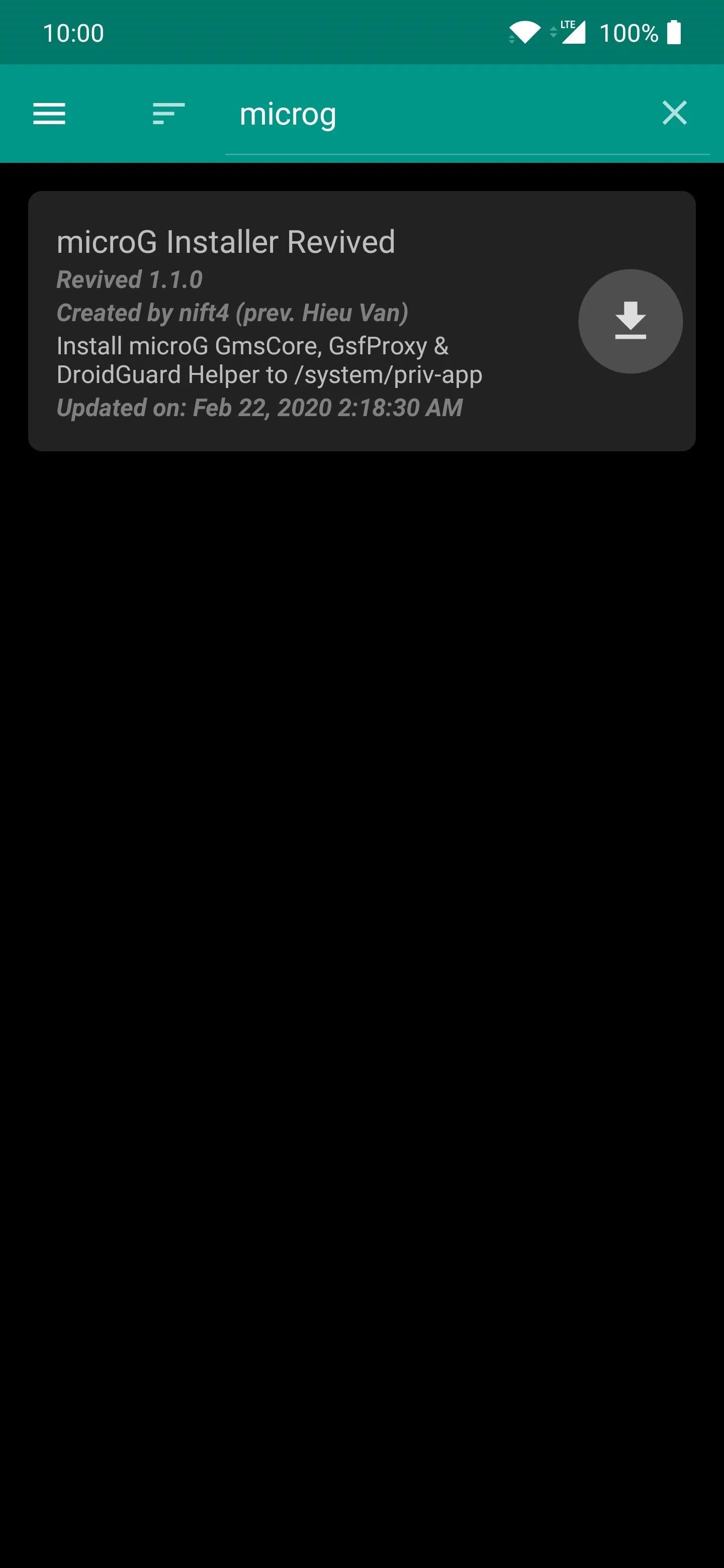
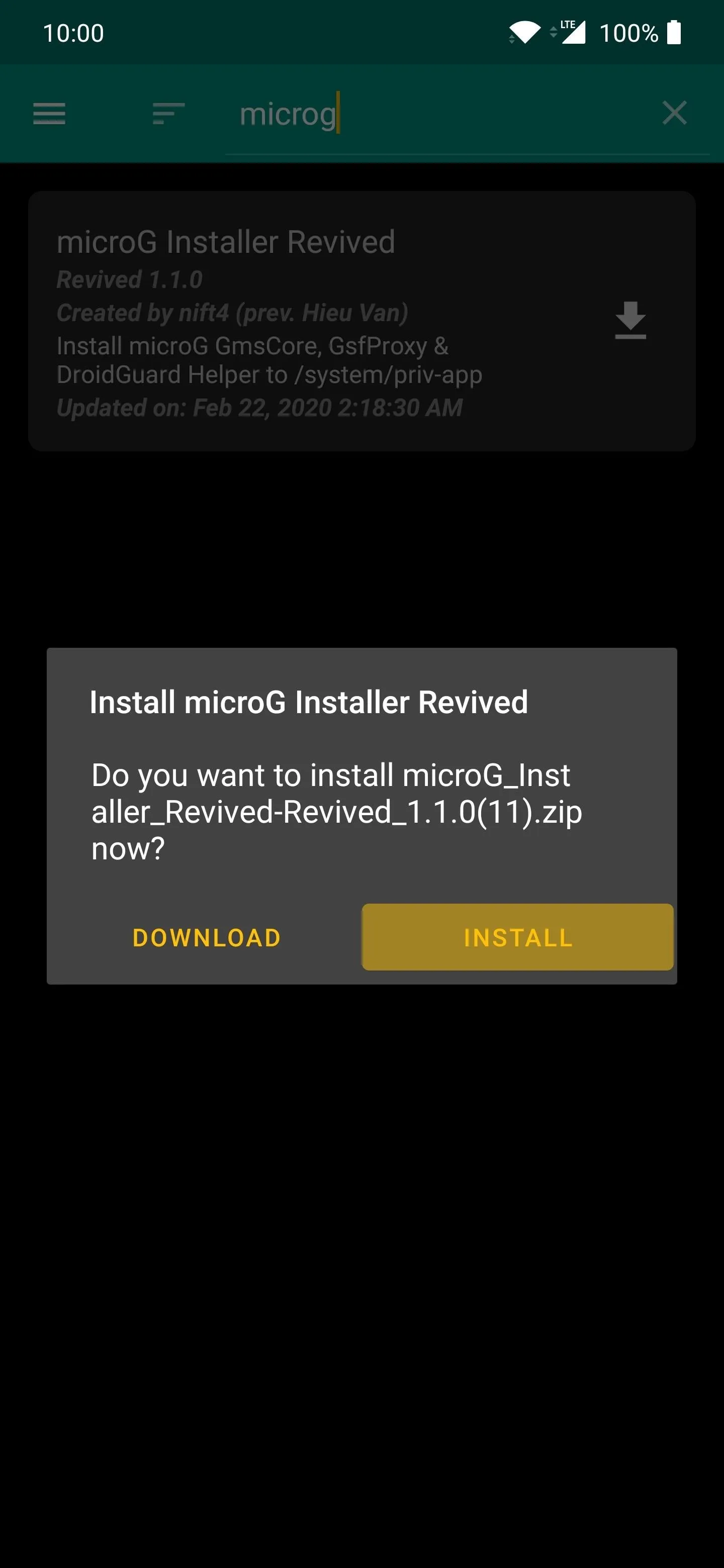
Open the Magisk Manager app to the main screen, tap the menu icon on the left, then head on over to the "Downloads" section. Tap the search icon the do a search for the term "microg," then the required module should pop up on the list right away as the only entry. Tap the download arrow once, then "Install" to get started.




Once the install process finishes, tap the reboot button to restart your system. Now you can head onto the next step below.
Step 4: Grant the Proper Permissions
Go into your app drawer, locate the Micro G app, then open it to the main screen. You might see a notification at the top, letting you know to grant permissions to the app. Expand the notification, tap "Request Missing Permissions," and then allow the permissions as requested. If you don't do this, your apps won't have access to the modified Google services, which defeats the purpose of MicroG.
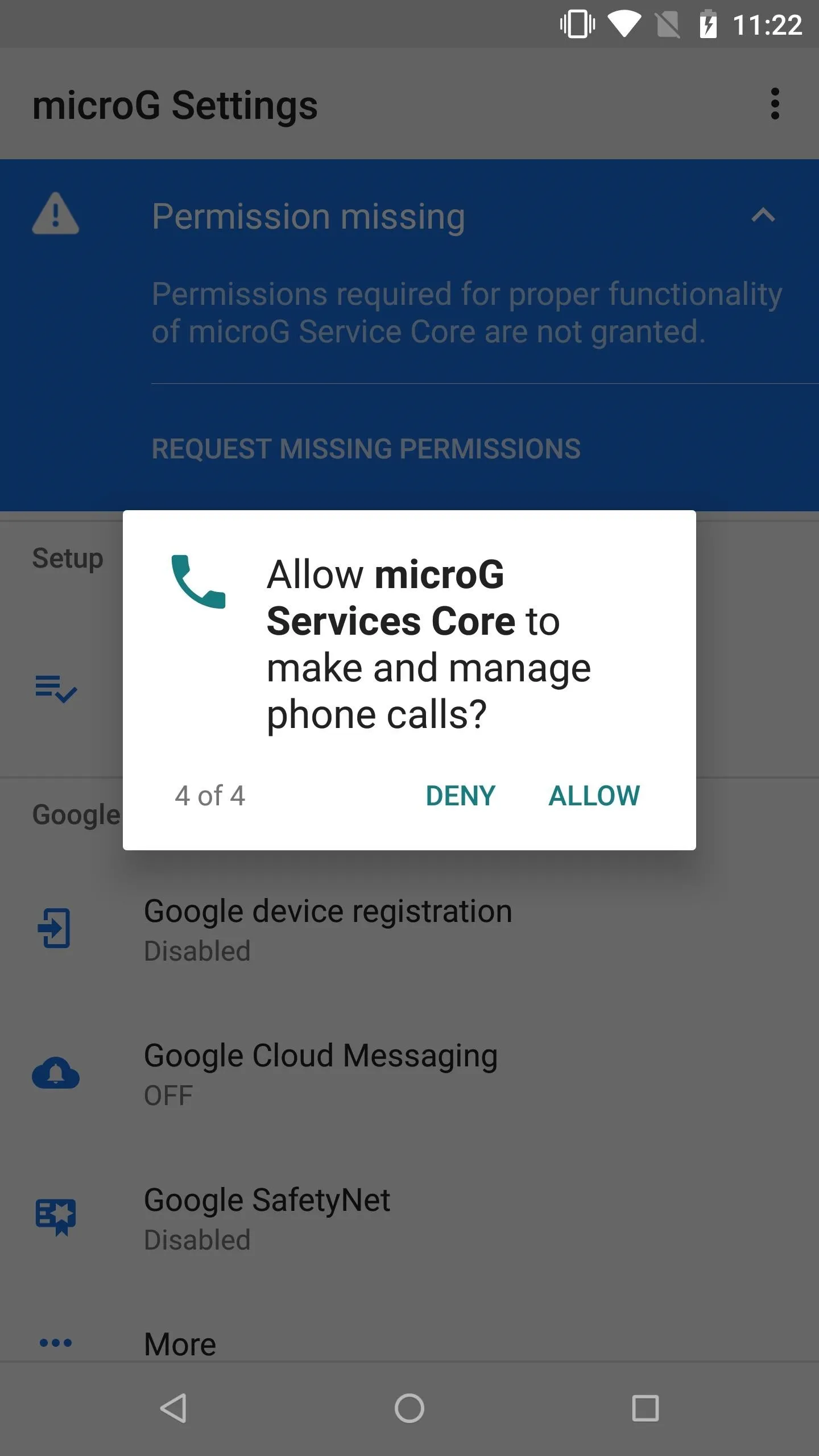
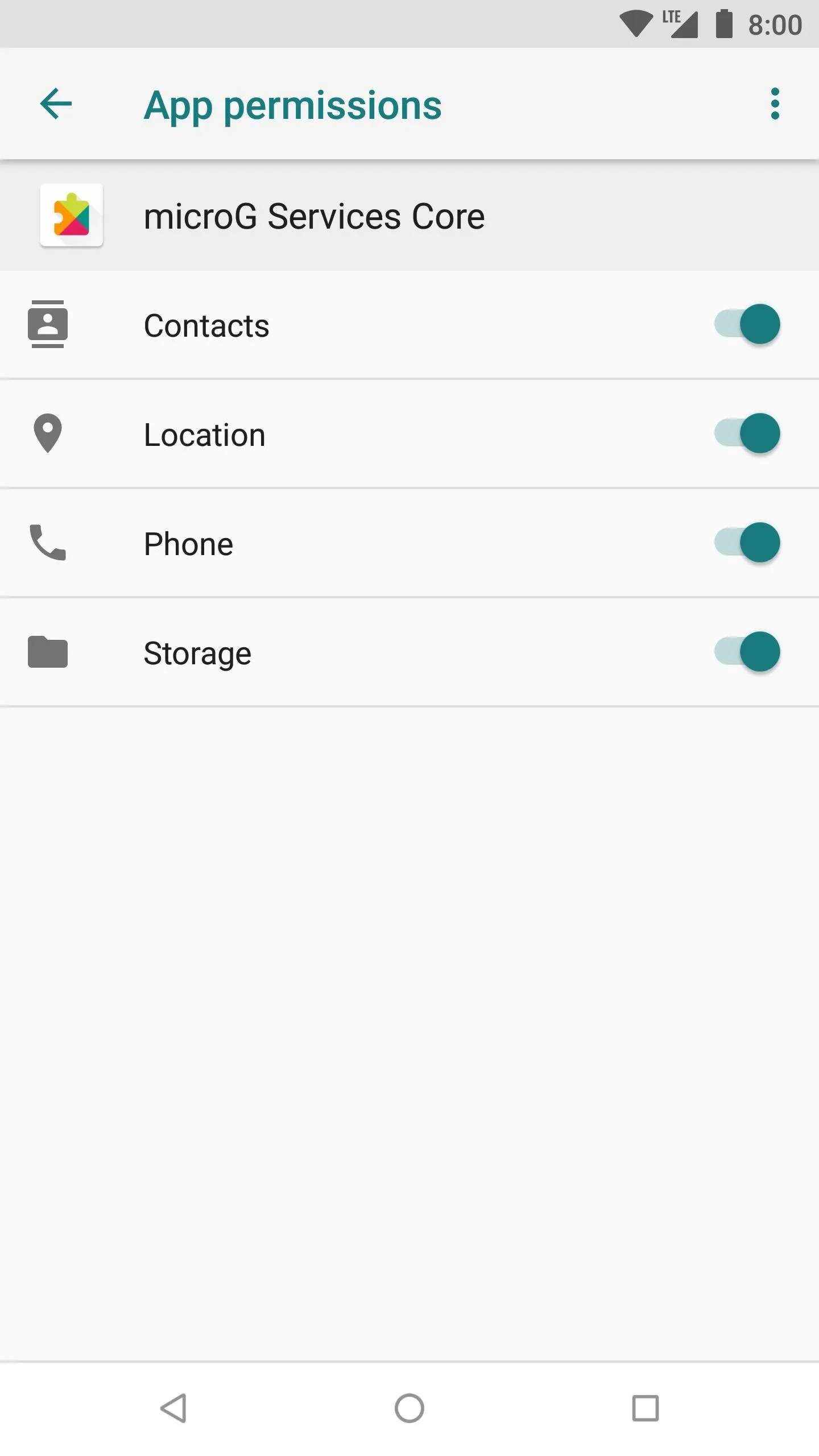


Step 5: Take the Self-Check Test
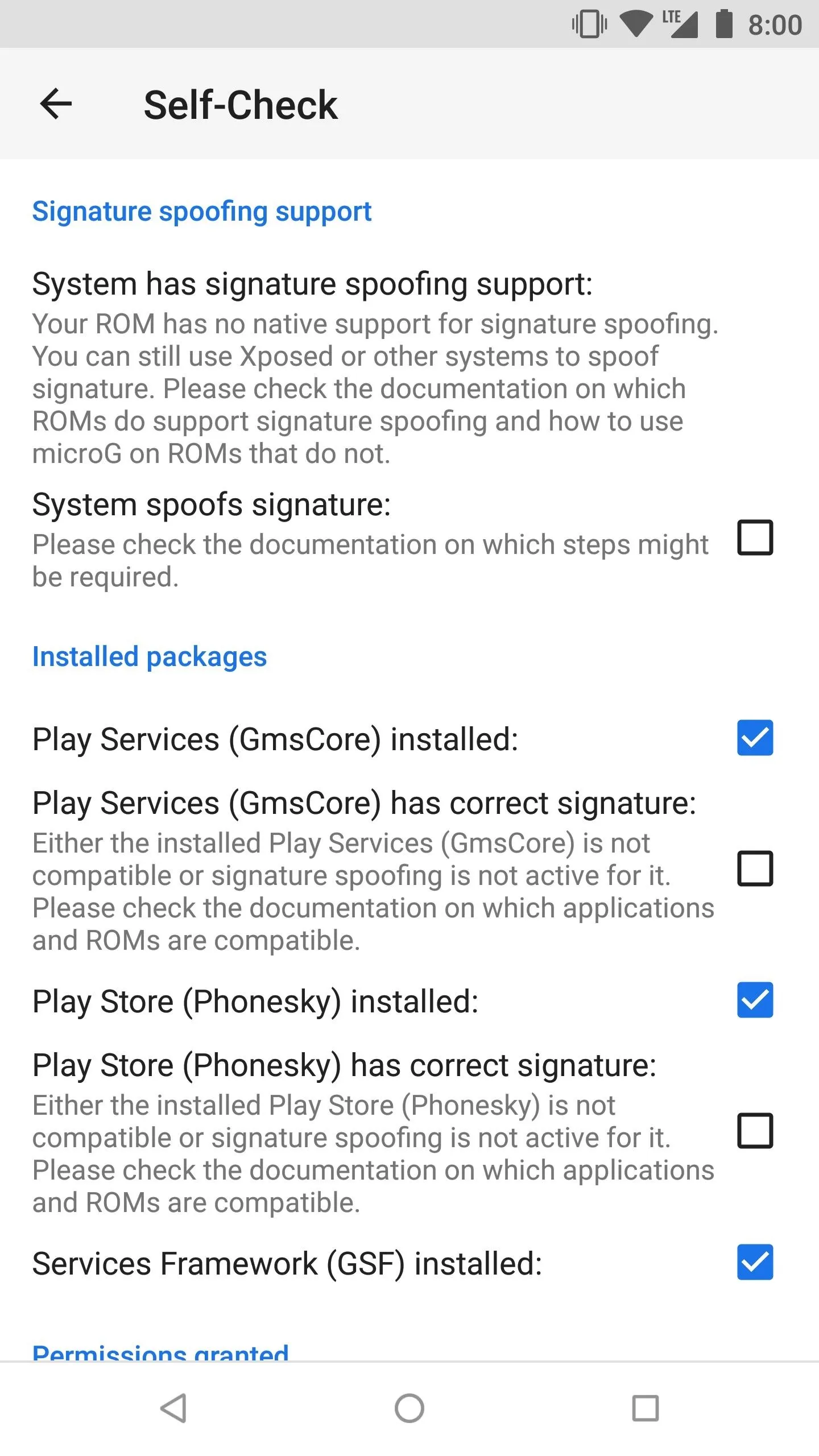
Open the MicroG app and tap the "Self-Check" section at the top of the screen. If your ROM supports signature faking mentioned from Step 1, the first checkbox should be checked. It will say, "System has signature spoofing support" if everything looks good from here.
You should also notice that just about everything else has an active checkbox, which is precisely what you want to see. If you're getting a message that says, "Your ROM has no native support for signature spoofing," then you need to go back to Step 1. At this point, you'd need to do a little more searching and find a custom ROM that does support signature spoofing before you can continue.
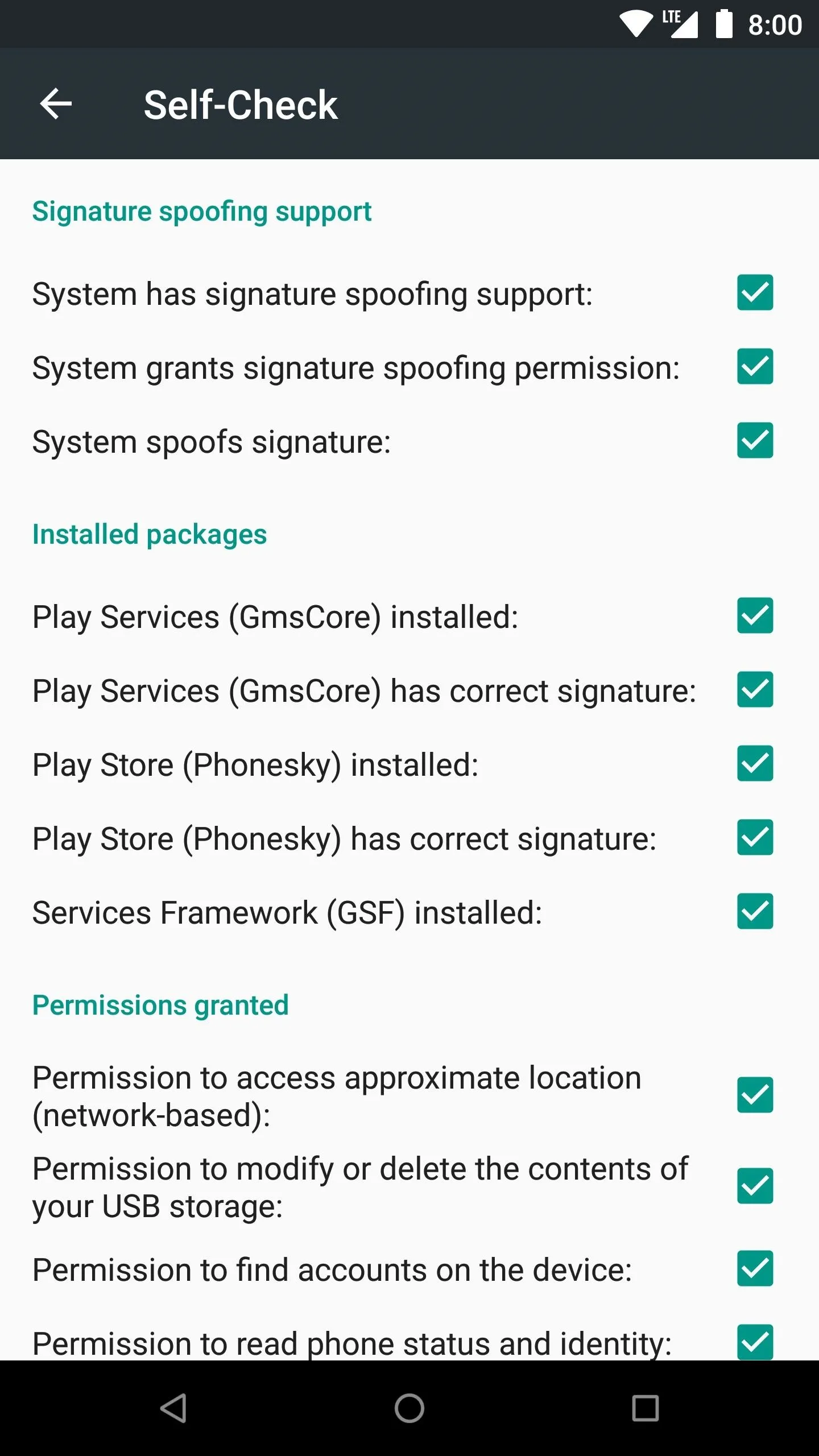
This is exactly what you want to see when doing the Self-Check test.
This is what it looks like when your ROM does not support signature spoofing.


This is exactly what you want to see when doing the Self-Check test.

This is what it looks like when your ROM does not support signature spoofing.
Your experience will not be great without signature spoofing, so you must get a custom ROM that supports it. Look at the documentation for the ROM, ask the developer, or even ask the community if you can't figure it out. Alternatively, you can flash a ROM and take the Self-Check test to find out in an instant. Once your custom ROM that passes the test, then you can move onto the next step.
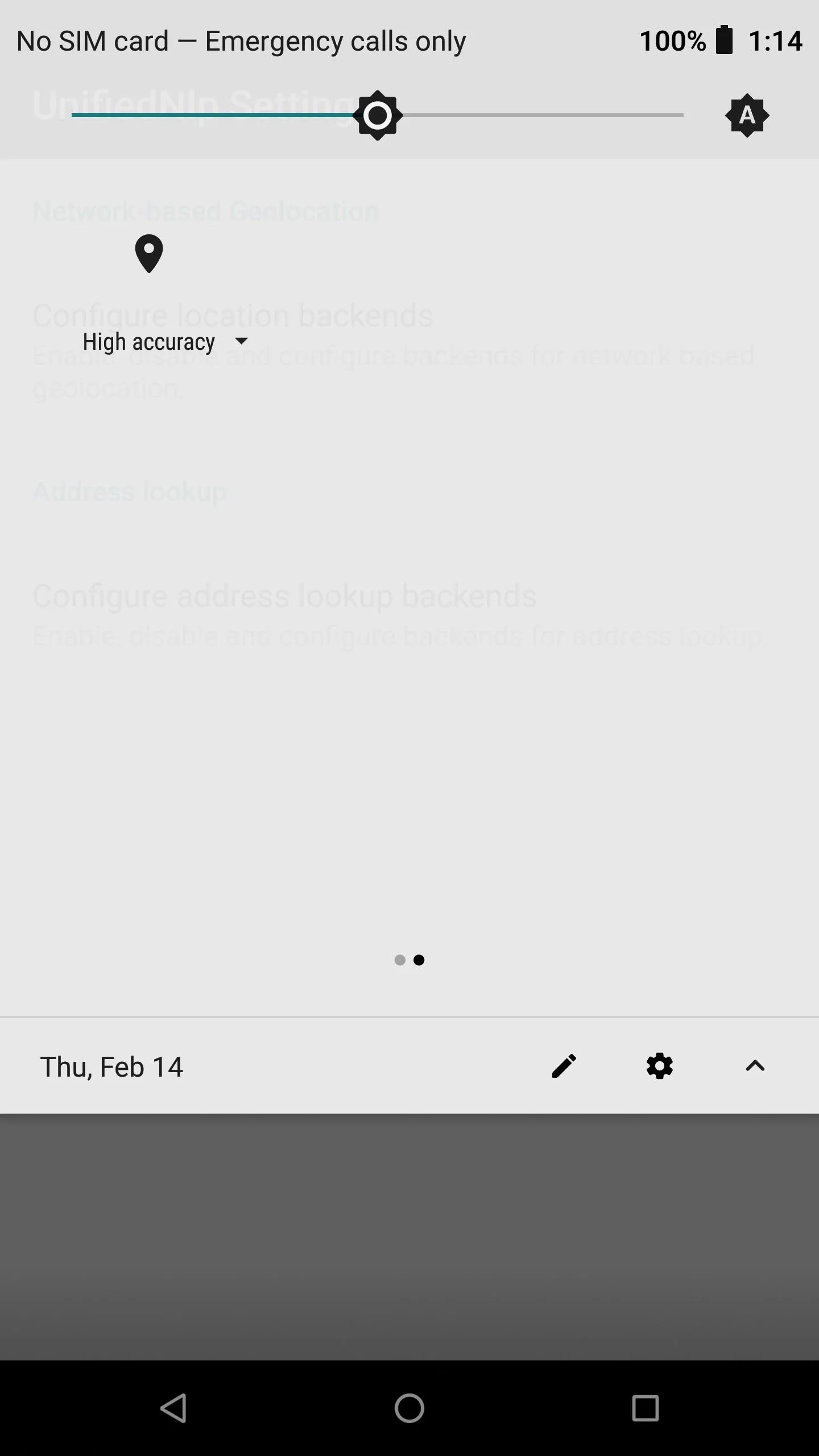
Step 6: Configure Location Services (Optional)
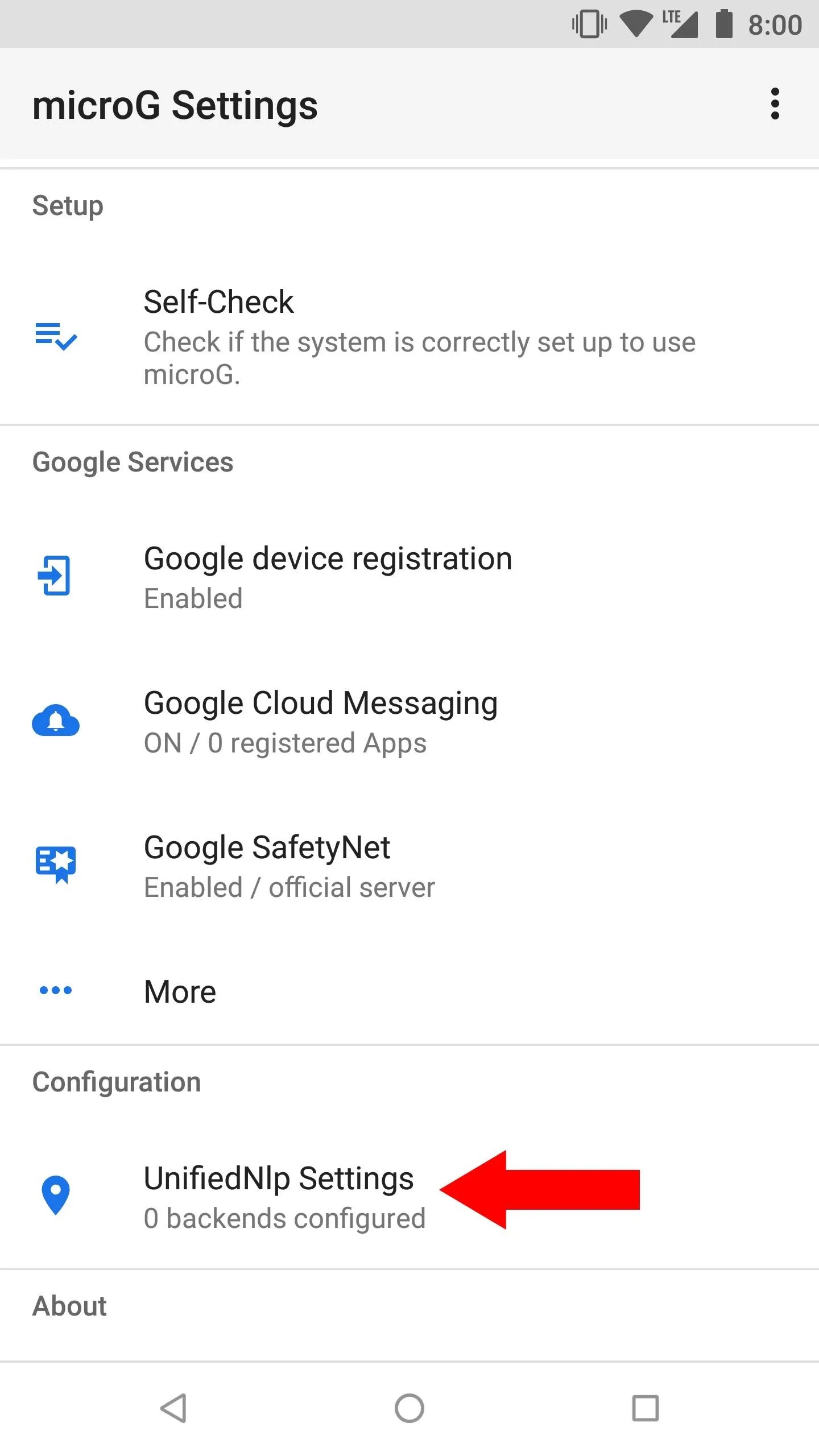
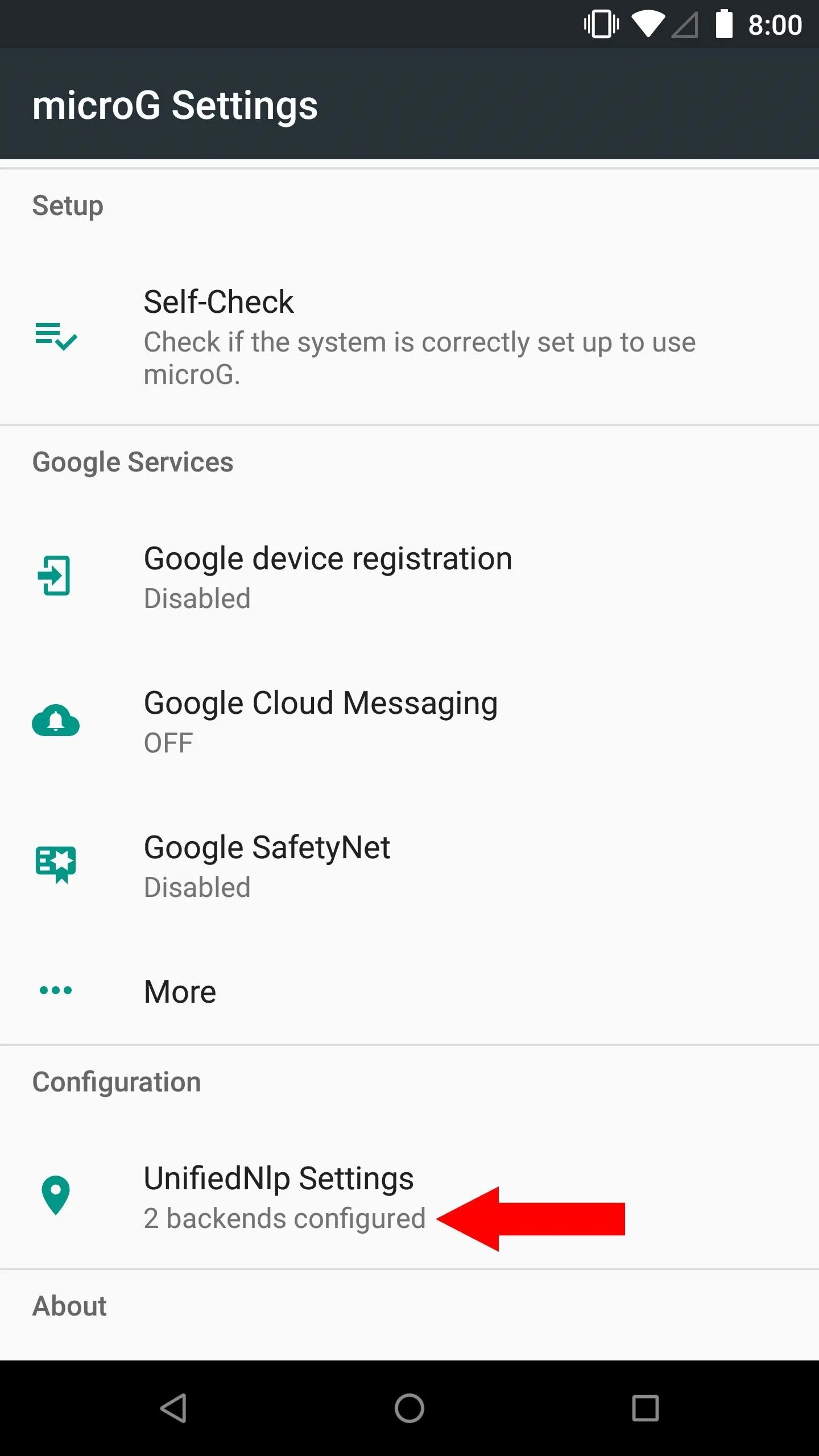
If you want to be able to use location services, such as GPS for maps or weather, you need to enable the options within the MicroG app. Since you are no longer relying on official Google Play Services to fetch your location data, MicroG handles it through the UnifiedNlp settings.
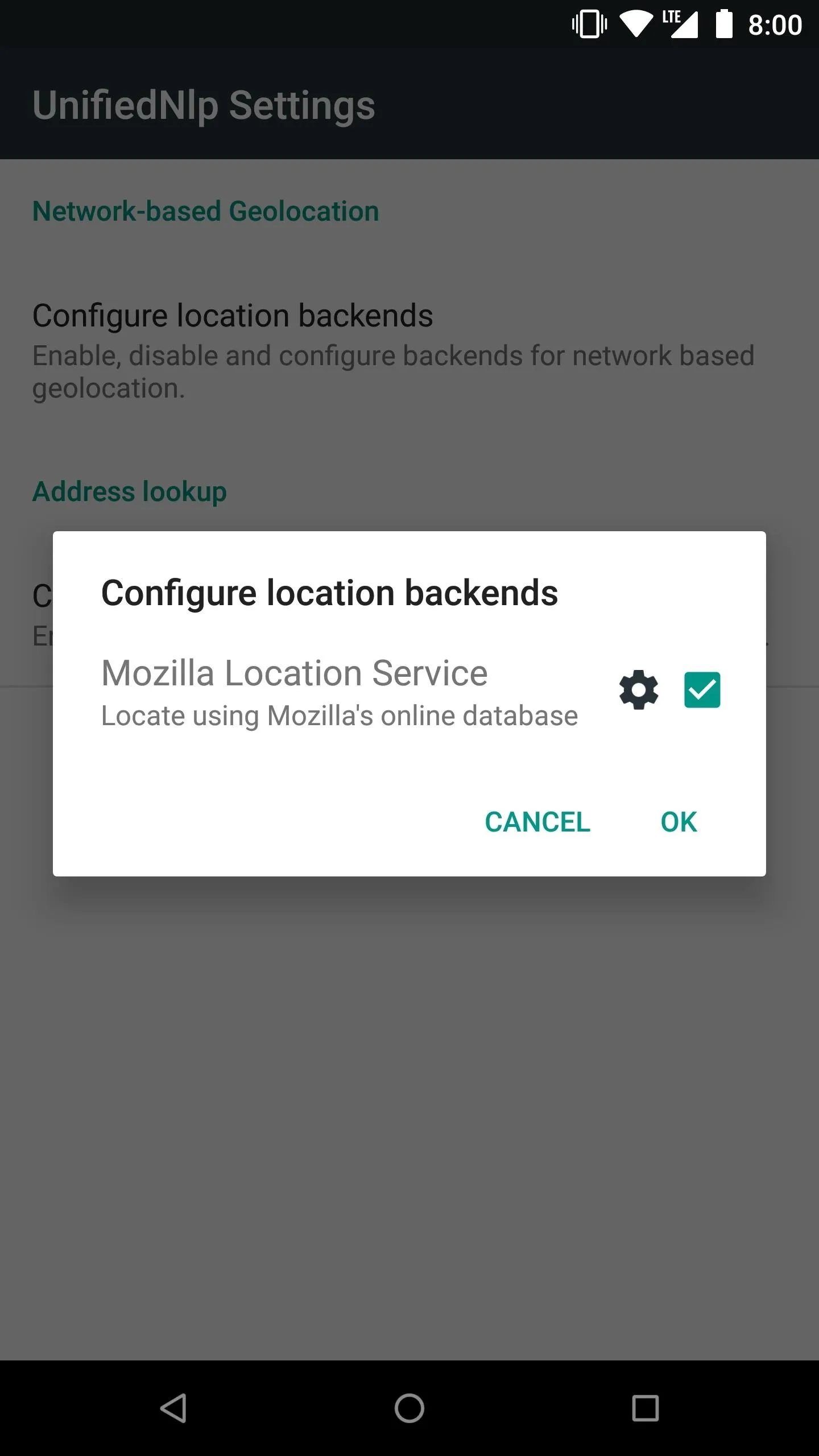
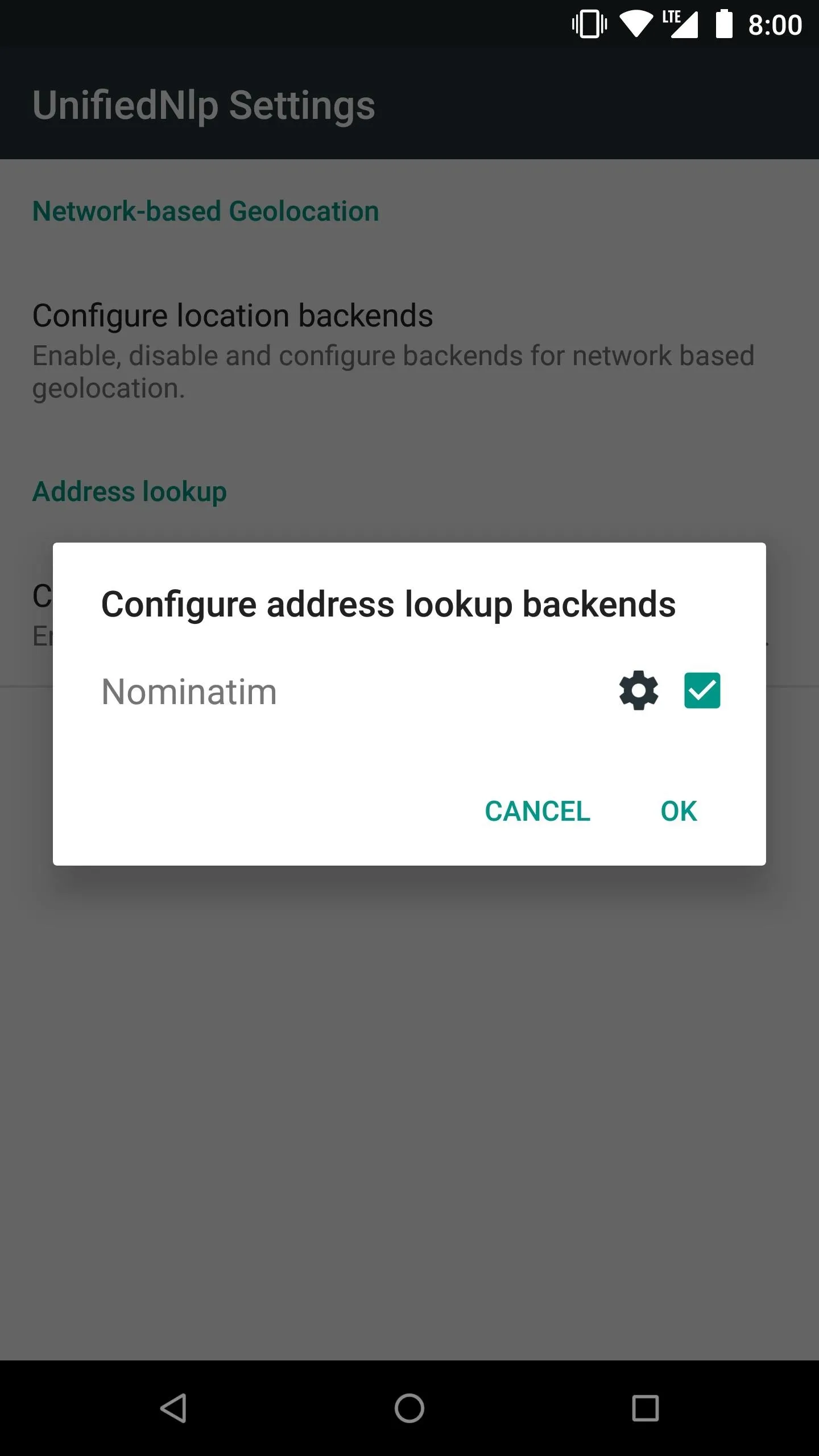
From the main screen on the MicroG app, tap "UnifiedNlp Settings," then "Configure location backends," and make sure Mozilla Location Service is checked. Tap "OK," then tap "Configure address lookup backends," and also make sure that "Nominatim" is checked as well.



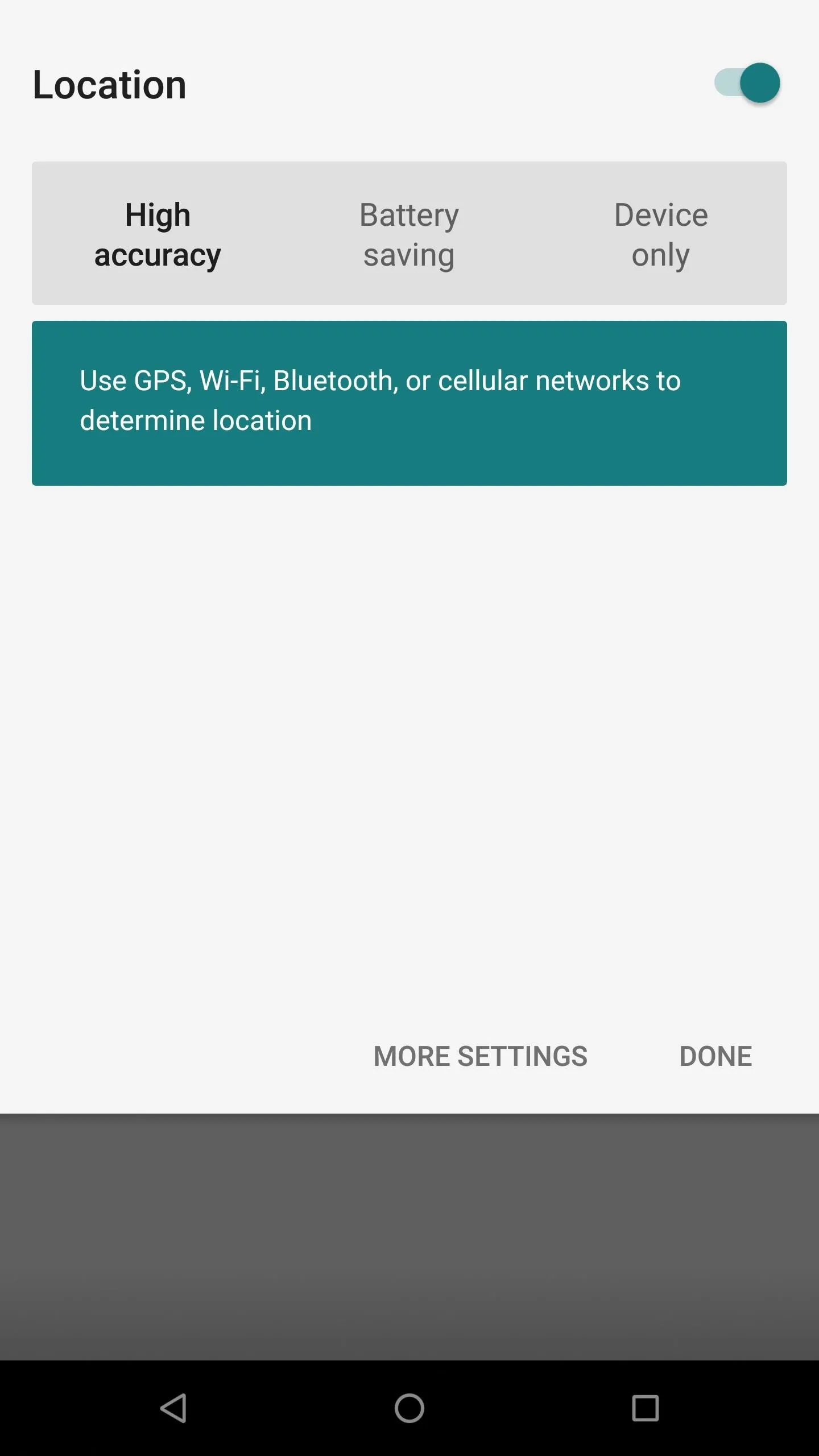
Bring up the quick settings from the status bar and make sure your location settings are on so you can use your new location services without Google. From this point on, GPS should work just like you were using the real Google Play Services. Now you can start building out your list of apps since you had to skip out on the default Gapps package. This was necessary to keep your privacy intact.



Don't forget that you can use MicroG with any custom ROM that supports signature faking. This ultimately means you'll have a wide variety of choices to pick from at any given time for your device. If you don't have a favorite ROM or don't know which works best for your needs, don't be afraid to experiment until you find a suitable choice. Good luck, and enjoy your increased level of privacy!
This article was produced during Gadget Hacks' special coverage on smartphone privacy and security. Check out the whole Privacy and Security series.
Cover image and screenshots by Stephen Perkins/Gadget Hacks



Comments
No Comments Exist
Be the first, drop a comment!